Enable Windows Authentication in IIS: This is a security mechanism for authenticating users based on their Windows credentials, typically within an organization’s network. When users try to access a resource or application, Windows Authentication checks their credentials (username and password) against a Windows domain or Active Directory. If a user is already logged into a Windows domain, they may not need to enter their credentials again for the application, providing a Single Sign-On (SSO) facility. It uses two primary protocols, NT Lan Manager (NTLM), and Kerberos. This post will guide you through the steps to enable Windows authentication in IIS on Windows 11 using simple yet clear steps. Let’s get started. Check out: Easy way to enable Digest Authentication for IIS on Windows 11
Table of Contents
Steps:
- Go to the Programs and Features window using the run command
appwiz.cpl- On the left pane, Click on Turn Windows Features on or off.
- Expand Internet Information Services node and futher expand World Wide Web Services.
- Finally, expand Security.
- Under Security, Enable Windows Authentication by clicking on the checkbox next to it and click OK.
- That is it. Windows Authentication in IIS optional feature is now enabled on your Windows 11 PC.
Directions to Windows Authentication on Windows 11
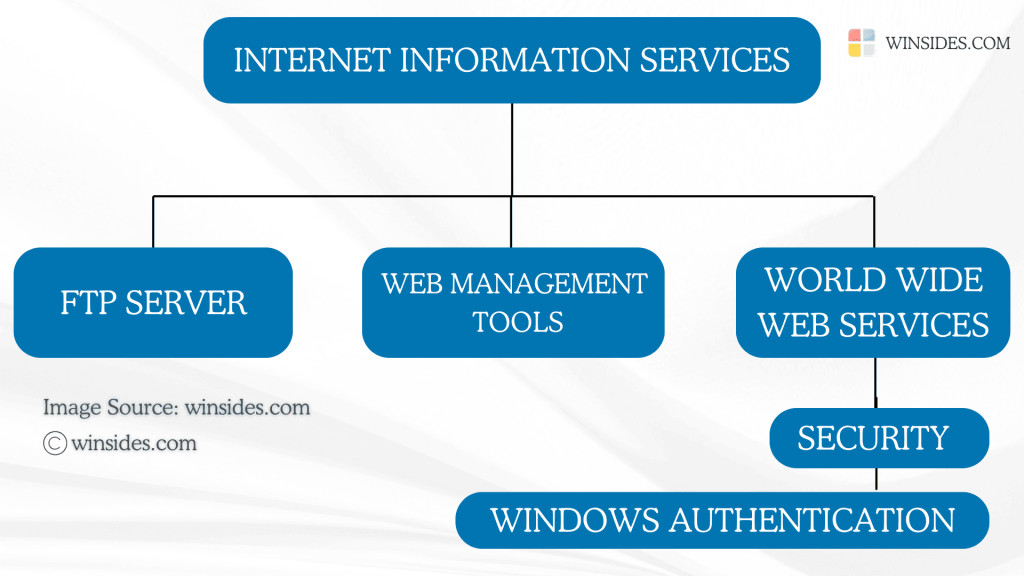
- Go to the Run command using the keyboard shortcut Win Key + R.
- Enter the following command
appwiz.cpland click OK. This command will open the Programs and Features window.
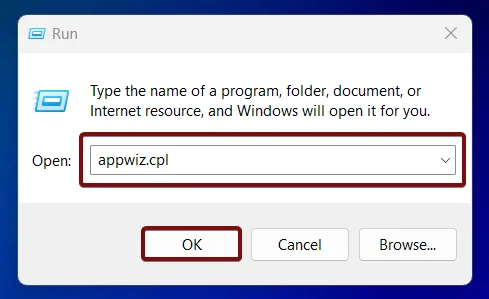
- The Programs and Features window will open now. Here, you can find Turn Windows Features on or off option from the left pane.
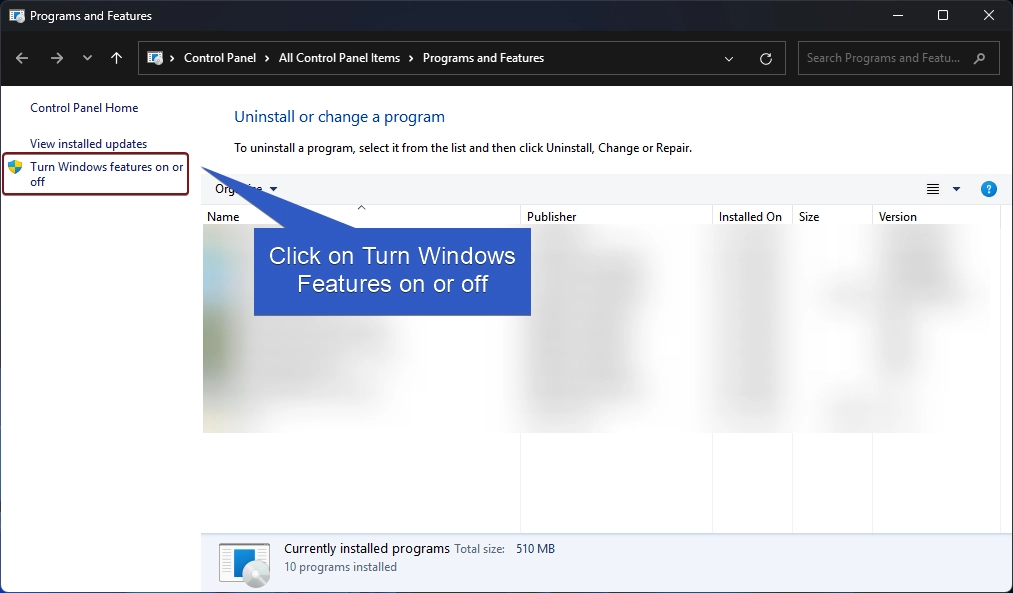
- Clicking on Turn Windows features on or off will open the Windows Features dialog. Here, you can find all the available optional features.
- Locate Internet Information Services from the list of services available and expand the tree.
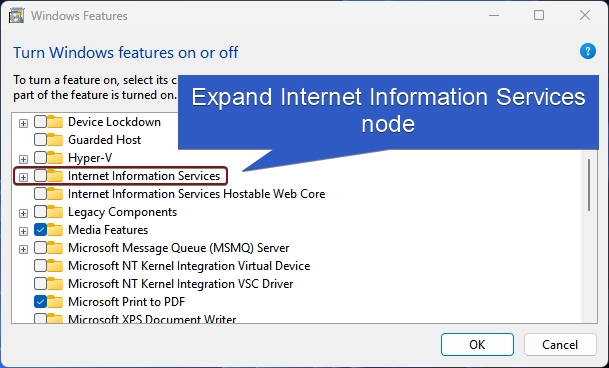
- Now, you will find FTP, Web Management Tools, and World Wide Web Services. We have to expand the World Wide Web Services.
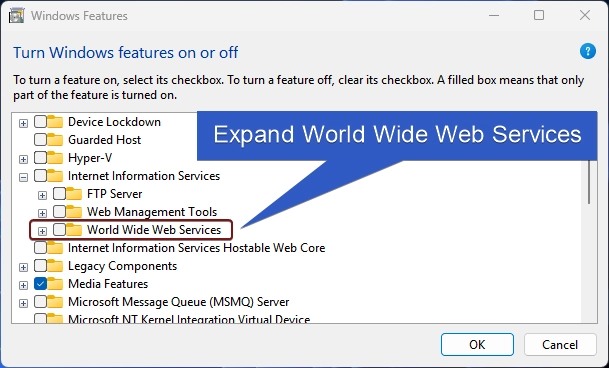
- You will find various features such as Application Development Features, Common HTTP Features, Health and Diagnostics, etc. Expand the Security node.
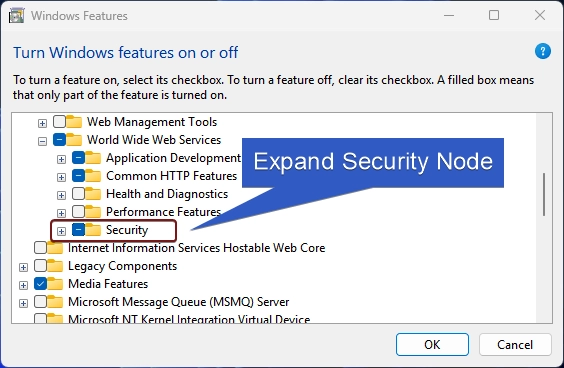
- You can find Windows Authentication. Click on the checkbox next to it to enable it and click OK.
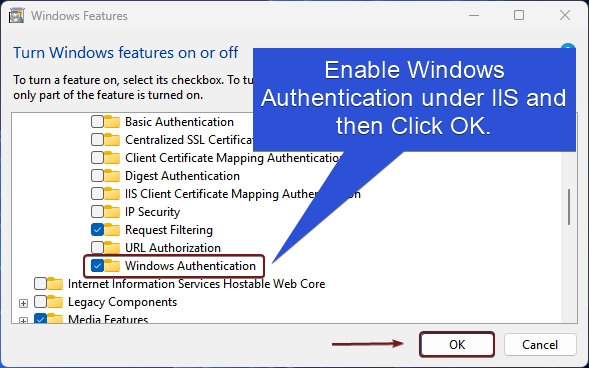
- Windows will now start searching for the required files.
- Then the system will apply the changes.
- Click on Close to Close the window. I suggest restarting the system to ensure that the changes are applied effectively.
Practical Scenarios where Windows Authentication can be helpful
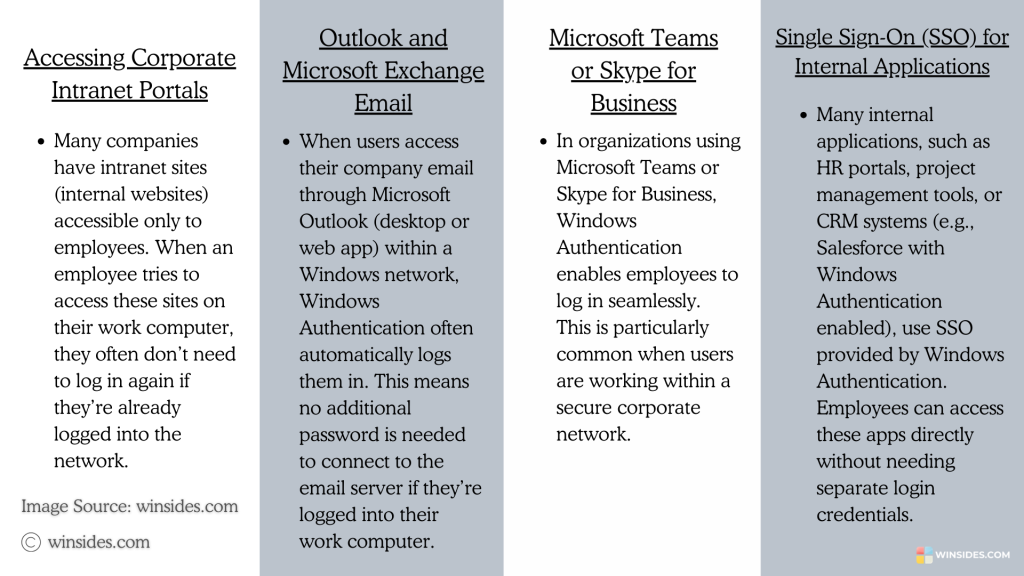
It is commonly used in workplace settings or internal systems where the users may not even realize they are being authenticated. Some of the applications include accessing corporate intranet portals where employees try to access company portals, users accessing their company email via Microsoft Outlook, accessing shared folders or mapped drives on a network, HR portals, Project Management tools, CRM systems, accessing printers or scanners in an organization, and more. In all these scenarios, if the user is logged in with his Windows username and password, Windows Authentication will authenticate automatically and the user to access the feature.
Frequently Asked Questions
Where is Windows Authentication commonly used?
Windows Authentication is commonly used in environments where users are part of a Windows domain, such as corporate intranets, internal applications, and applications hosted on Internet Information Services (IIS) for internal network access.
What is the difference between NTLM and Kerberos in Windows Authentication?
NTLM is an older protocol and is generally less secure than Kerberos. It’s used in workgroup environments or where Kerberos isn’t supported. Kerberos is the preferred protocol in Windows domains because it is faster, more secure, and supports mutual authentication.
What is Integrated Windows Authentication (IWA)?
Integrated Windows Authentication (IWA) is a feature that allows users to authenticate automatically based on their Windows credentials. It is commonly used in environments where a seamless user experience is desired, as it eliminates the need for repeated logins.
Is Windows Authentication secure?
Yes, Windows Authentication is secure, especially when using the Kerberos protocol.
Take away
Windows Authentication in IIS on Windows 11 is a powerful and secure authentication method ideal for organizations operating within a Windows domain. However, in non-Windows or cross-platform scenarios, it requires additional configuration. It is a valuable tool for enterprises and IT administrators looking to secure internal applications, file shares, and network resources. We hope you are satisfied with our article. For more interesting articles, stay tuned to Winsides.com. Happy Configuring! Peace out!
Like our Article?
If you have any queries, do let us know in the comment section. We love to hear from you.
![How to Enable IIS [Internet Information Services] in Windows 11? 1 Enable IIS in Windows 11](https://winsides.com/wp-content/uploads/2024/01/IIS-in-Windows-11-390x220.webp) How to Enable IIS [Internet Information Services] in Windows 11?
How to Enable IIS [Internet Information Services] in Windows 11? How to Enable Simple TCP/IP Services in Windows 11?
How to Enable Simple TCP/IP Services in Windows 11? Enable SMB 1.0 / CIFS File Sharing Support using Command Prompt & Windows PowerShell
Enable SMB 1.0 / CIFS File Sharing Support using Command Prompt & Windows PowerShell Enable SMB 1.0/CIFS File Sharing Support in Windows 11
Enable SMB 1.0/CIFS File Sharing Support in Windows 11