Easy way to Enable Request Filtering in IIS on Windows 11
Configure Rules to block selected Client Requests.
Request Filtering in IIS is a security feature that allows administrators to control which HTTP requests the server processes. It helps protect the server from malicious requests and optimize its performance by filtering out potentially harmful requests. It is an optional feature and can be enabled via the Windows Feature of Windows 11 OS. In this article,we will check out How to Enable Request Filtering in IIS on Windows 11 using simple steps. Check out:How to Enable URL Authorization of IIS on Windows 11
Table of Contents
Key Steps:
- To Enable this feature on Windows 11,we will use Windows Features.
- To access Windows Features,open Run and execute the following command.
appwiz.cpl- On the Programs and Features window,click on Turn Windows Features on or off from the left pane.
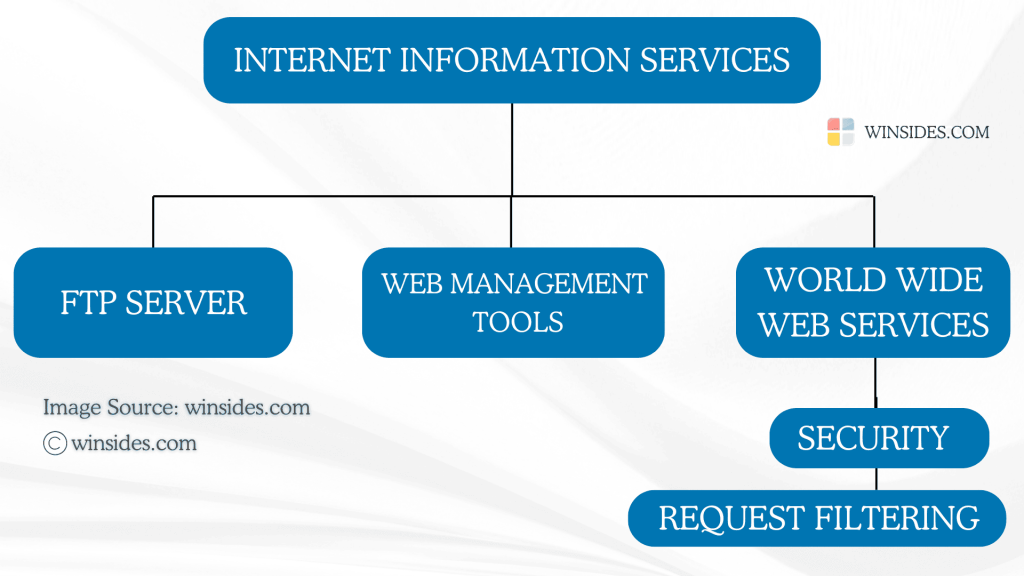
- Windows Features dialog will open now. Locate Internet Information Services and expand the tree.
- Then,expand World Wide Web Services.
- Finally,expand Security.
- Now,you can find Request Filtering Click on the checkbox to enable it. Click OK.
- That is it. The system will enable Request Filtering in IIS.
Directions to reach Request Filtering in IIS on Windows 11
Let’s get started.
- Go to the Run command using the keyboard shortcut Win Key + R.
- Enter the following command
appwiz.cpland click OK. This command will open the Programs and Features window.
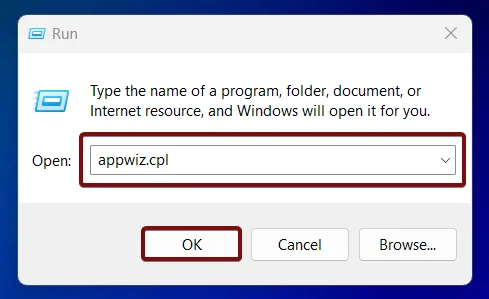
- The Programs and Features window will open now. You can find Turn Windows Features on or off option from the left pane.
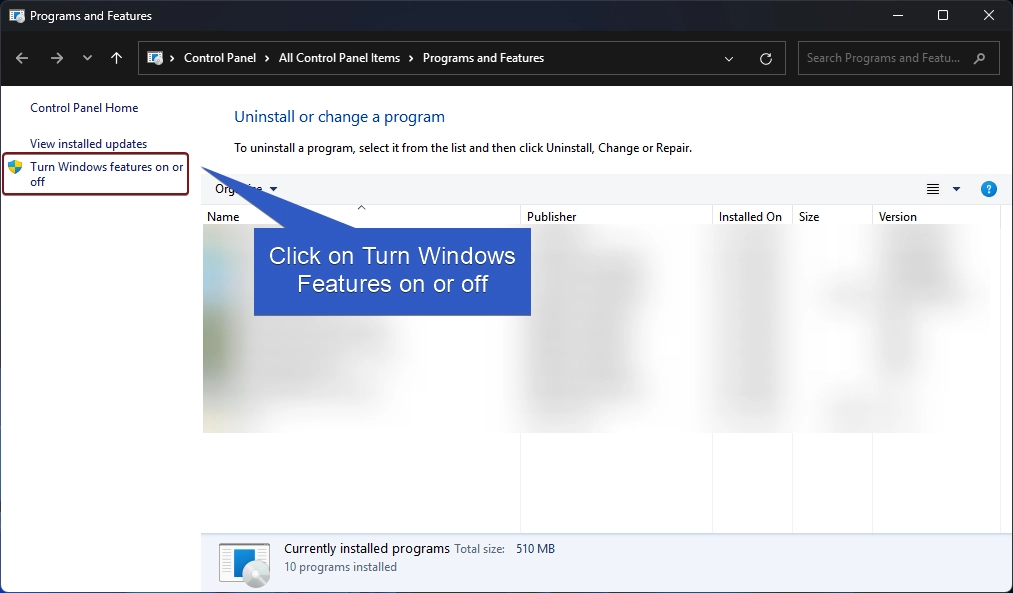
- Clicking on Turn Windows features on or off will open the Windows Features dialog. Here,you can find all the available optional features.
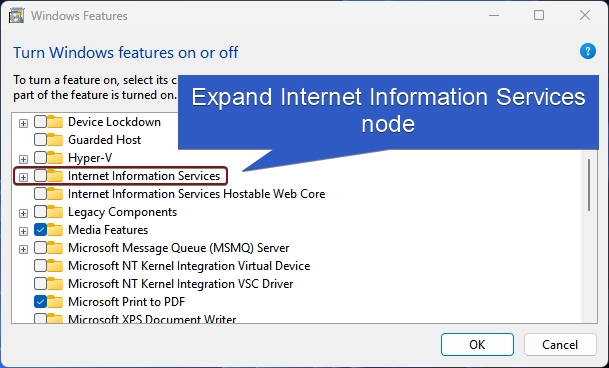
- Locate Internet Information Services from the list of services available and expand the tree.
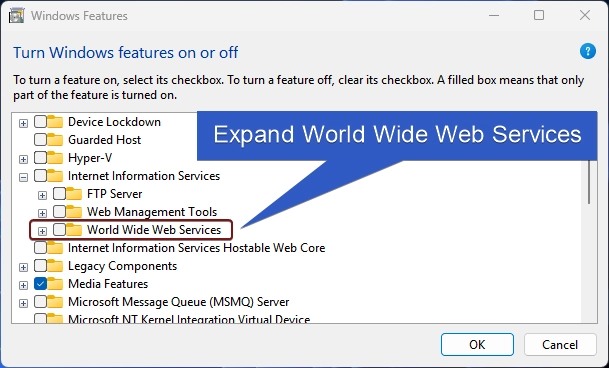
- Now,you will find FTP,Web Management Tools,and World Wide Web Services. We have to expand the World Wide Web Services.
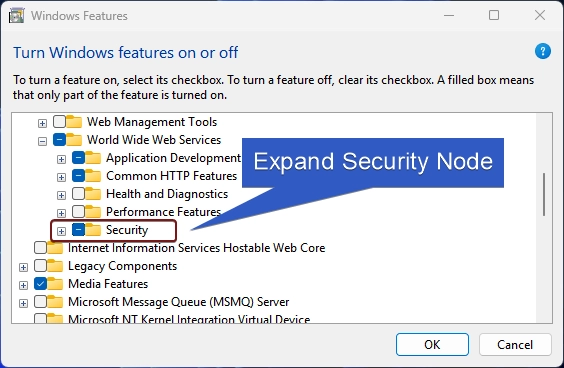
- You will find various features such as Application Development Features,Common HTTP Features,Health and Diagnostics,etc. Expand the Security node.
- You can find Request Filtering. Click on the checkbox next to it to enable it and click OK.
- Windows will now start searching for the required files.
- Then the system will apply the necessary changes.
- Click on Close to Close the window. A Restart is highly recommended.
- That is it. Request Filtering for IIS is now enabled on Windows 11 OS.
Request Filtering in IIS –Feature availability on various Windows Editions
This section provides information on the availability of this feature on different Windows Editions.
| Windows Editions | Availability |
| Windows 11 Home | No |
| Windows 11 Professional | Yes |
| Windows 11 Education | Yes |
| Windows 11 Enterprise | Yes |
| Windows 11 Pro Education | Yes |
| Windows 11 SE | No |
| Windows 11 IoT Enterprise | Yes |
Key Functions of Request Filtering in IIS:
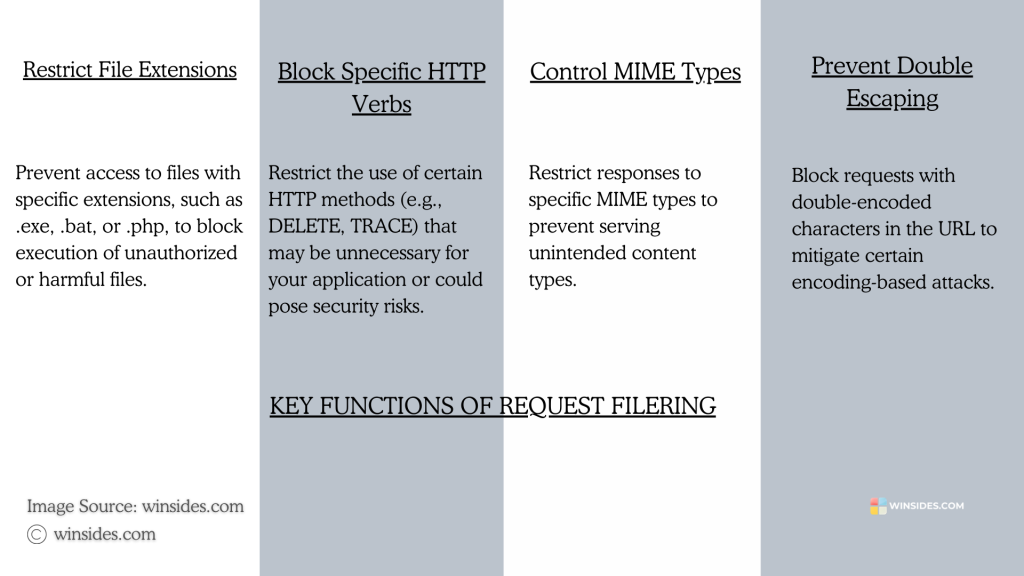
The main purpose of this feature is to restrict harmful access requests. It includes
- Restrict File Extensions
- Set Request Size Limits
- Block Specific HTTP Verbs
- Filter URL Sequences
- Deny Hidden Segments
- Control MIME Types
- Prevent Double Escaping
- Deny Unlisted Extensions
- Configure Verbose Error Responses
Information on the Go
Request filtering ensures that only legitimate requests are processed by the server,protecting it against common attack vectors such as SQL injection,cross-site scripting (XSS),and denial-of-service (DoS) attacks. It also enhances server performance by reducing the processing of unnecessary or harmful requests.
Can Request Filtering block directory traversal attacks?
Yes,by using the URL Sequences filter,you can block character patterns like ../ or encoded equivalents (%2e%2e/) to prevent directory traversal attacks.
How do I allow or block specific file extensions in IIS?
Go to Request Filtering in IIS Manager. Select File Name Extensions in the Actions pane. Add extensions to allow or deny (e.g.,.exe → Deny).
What happens when a request is blocked by Request Filtering?
When a request is blocked,IIS returns a 403 Forbidden response or another custom error message based on your configuration.
Can Request Filtering be customized for specific applications or sites?
Yes,it can be applied on the Server Level,Site Level,and Application Level.
Take away
Request Filtering in IIS acts as a frontline defense against malicious attacks such as directory traversal,buffer overflow,and unauthorized file access. However,it is highly recommended to use comprehensive security strategies that include application-level safeguards,Firewalls,and Regular Monitoring. I hope you are satisfied with our article and if you have any queries,kindly let us know in the comment section. For more IIS-related articles,stay tuned to Winsides.com. Happy Coding! Peace out!
We combine expert insights with user-friendly guidance. We thoroughly research and test everything to give you reliable and simple to understand tech guides. Please take a look at our publishing process to understand why you can trust Winsides.